
Secure Your Organization With Our Comprehensive Cybersecurity Solutions And 24x7x365 Security Operations Centre (SOC)
Cybersecurity Made Simple With All-In-One Threat Detection, Analysis, and Response
You need a cybersecurity solution built to match the evolving needs of your modern business. MDR, XDR, EDR, SIEM, SOC… no matter what acronym you’re looking for, it’s all under the hood of our cybersecurity suite.
A Holistic, 24/7 Managed Cyber Security Solution
The unique strength of our cyber security suite is that it not only provides visibility into every aspect of your threat surface, but it aggregates the data from multiple security events into simple, actionable steps:
No Security Expertise Required
No More Alert Fatigue
Deployed In Minutes
Pricing Tailored To The SME (Small-Medium Enterprise)
Our Incident Response (IR) Team Is Certified With Most Cyber Insurance Companies
CALL FOR A FREE SECURITY ASSESSMENT | 604-986-8568
Most Businesses Have No Idea How Vulnerable They Are. We Offer a Complimentary (No Obligation) Mini-Security Penetration Test Designed To Let You Know Exactly What Your Risk Exposure Would Be If You Or Your Staff Clicked On Something That You Shouldn't Have. 95% Of Organizations Are Under-prepared For A Cybersecurity Incident Of This Type.

Secure Your Business Today!
We Cover All Aspects Of Your Security
End-to-end protection
Backed by sophisticated technology and human intelligence, get best-in-class 24x7x365 cyber security, actionable alerts, and a greater return on investment.
Endpoint security
With support for all major platforms— our cybersecurity suite detects and resolves attacks and vulnerabilities on your endpoints.
Network security
Our cybersecurity suite combines best-in-class network threat monitoring technology with hands-on, 24/7 support from cyber experts to identify and resolve network-based threats.
Cloud-based security
Access in-depth monitoring and threat protection for the cloud-based services you use every day, including Microsoft 365, Google Workspace, Azure, AWS, Dropbox, Box.com, and more.
Remote workplace connectivity
Protect your remote workers with LAN ZeroTrust technology, and experience our always on, always connected secure access edge platform to securely connect your remote workers with the data and resources that they nee.
Staff cybersecurity resilience training
Provide your staff with on-going cybersecurity awareness training, phishing simulations, and a secure and convenient Canadian-hosted Digital Password Manager.
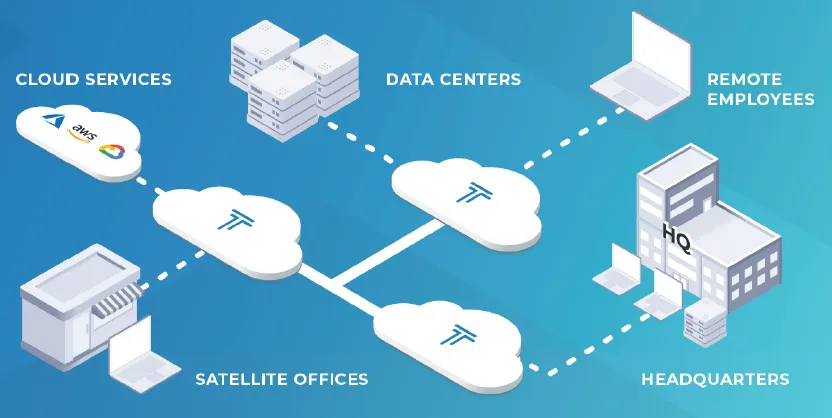


24/7 Network traffic analysis
Secure your network by analyzing all network traffic, including known and unknown devices, Internet of Things (IoT) devices, and mobile devices. Identify and respond to threats and potential vulnerabilities to your network.
Complete endpoint threat detection & response
Protect all your endpoints—including servers, desktops, and laptops—and identify anomalous behaviour to actively block known and emerging malware and attack techniques.
Active malware and APT protection
Automatically identify and block malware, ransomware, and advanced persistent threats (APTs) using policies and technology informed by leading cyber expertise.
Cloud layer detection and response
Use our cloud-native monitoring sensor to protect your company domain and cloud-based programs and applications, including Microsoft 365, Google Workspace, Amazon Web Services, Azure, Dropbox, Box, Okta, Salesforce, and more.
Fortify your network perimeter
Rely on our DNS firewall to ensure safe web browsing and Internet access by blocking connections to malicious websites.
Mitigate vulnerabilities and risks
Identify important changes and activity across your IT environment that indicate risks—including misconfigured cloud services and unpatched software—and receive detailed steps to resolve issues and improve your security.
Access advanced analytic engine
Benefit from machine learning and analytic capabilities that provide continuous analysis of user and service data to identify and address threats. The result is real-time visibility to detect, monitor, measure, manage, and reduce attackable points from end to end.
Gain expert threat hunting
Obtain better insight and security recommendations thanks to our expert threat hunters who dive deep into network and data to identify new, emerging, or otherwise undetected vulnerabilities and threats.
Experience active response
Automatically block malware, isolate devices, or take further action to protect your business. Our cybersecurity suite takes appropriate action on your behalf and based on your risk tolerance, always backed by human analysis.
Prioritize security efforts
Implement security controls, user policies, and education efforts through targeted insights and guidance from our intelligent Actions, Recommendations, and Observations (AROs) alerts and reporting.
Flag suspicious email activity for expert review
Protect email communications with our Suspicious Email Analysis Service, enabling users to quickly forward any suspect emails to our cyber experts for fast analysis.
Align with cyber security frameworks
Experience advanced vulnerability discovery and reporting based on industry best practice frameworks, including the NIST Cyber Security Framework, ISO 27001, Canadian Centre for Cyber Security Baseline Controls (CCSC BC), Payment Card Industry Data Security Standard (PCI DSS), and Australia’s ACSC Essential Eight Mitigation Measures.
Access round-the-clock security expertise
Get help every step of the way. Expert cyber analysts are available for your security questions, providing the advice you need.

What Our Clients Say



Secure Your Business Today!
Businesses of all sizes should have access to world-class cyber security. By implementing our cyber security suite, they do!
Book your no-obligation 30 minute discovery call today!
Call 604 986-8568
E-mail: sales@itideas.com
Contact Us
15th Floor – 701 West Georgia Street
Vancouver, BC V7Y 1G5
Phone: 604 986-8568
E-mail: sales@itideas.com
Copyright © 2023. All rights reserved.